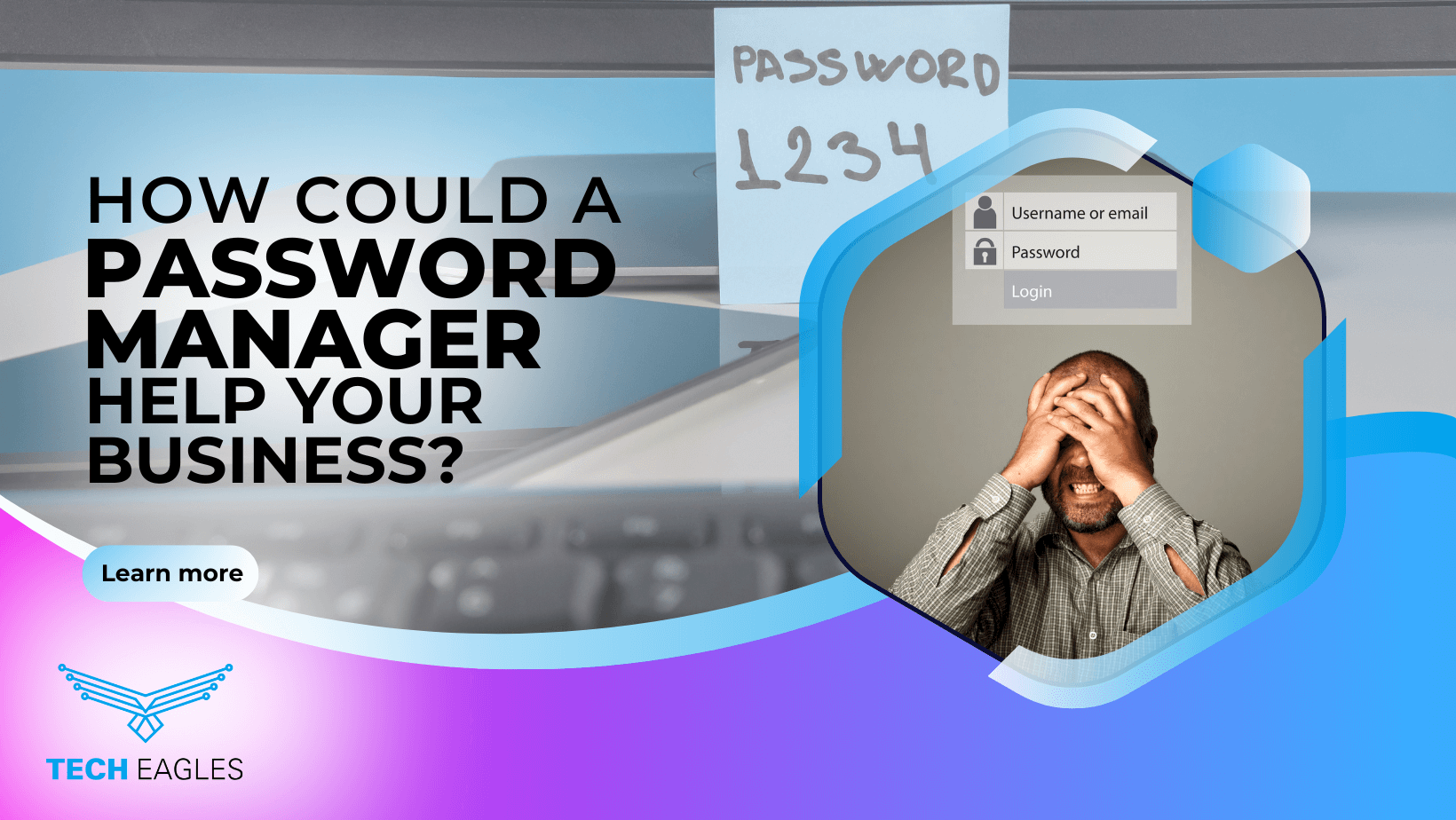
Strengthen Your First Line of Defense. Best Practices for Password Security.
Rachel | November 12, 2025
With most, if not all, aspects of business now digitized, the need for credential security is paramount. Credential theft has become the most damaging threat for businesses today. Cybercriminals use a multitude of ways to gain access to business credentials…
READ MORE